About Us
Home / About Us
About Us
The Data Initiative was established to empower our hospital partners to ethically invest in their
futures by harnessing artificial intelligence for actionable insights that enhance every
aspect of their operations.
Our co-investment model reduces costs and maximizes the benefits derived from large language
models and AI technologies. By bridging advanced technology with everyday healthcare practices,
we ensure that AI solutions enhance patient care without compromising ethical standards.
Disciplined & Responsible Artificial Intelligence
Services Offered
AI Consultation and Strategy: Tailored strategies to implement AI with minimal risk and maximum impact.
Healthcare AI Integration: From natural language processing for clinical documentation to machine learning for diagnosis and patient engagement.
Revenue Cycle Management: Leveraging AI to enhance every aspect of the revenue cycle, from patient intake to final billing.
Data Centralization and Analysis: Ensuring that providers can offer the best patient care through comprehensive data analysis and centralized data formats.
Ethical AI Deployment: Guiding healthcare providers on the legal, moral, and ethical use of AI without compromising patient welfare or data integrity.

Compliance





HIPAA
The Health Insurance Portability and
Accountability Act of 1996 (HIPAA) is a federal law that required the creation of national standards to protect sensitive patient health information from being disclosed without the patient's consent or
knowledge.
FERPA
The Family Educational Rights and Privacy Act of 1974 is a United States federal law that governs the access to educational information and records by public entities such as potential employers, publicly funded educational institutions, and foreign
governments.
HITECH
The Health Information Technology for
Economic and Clinical Health Act (HITECH Act) was signed into law as part of the American Recovery and Reinvestment Act (ARRA) bill in 2009 to drive the adoption and meaningful use of electronic health records
(EHR) technology by US-based healthcare providers and their business associates.
SSAE-16
16 (SSAE 16) is a set of auditing standards and guidance on using the standards, published by the Auditing Standards Board (ASB) of the American Institute of Certified Public Accountants (AICPA), for redefining and updating how service companies report on compliance controls.




DIACAP
(US Department of Defense Information Assurance Certification and Accreditation Process) Superseding the earlier DITSCAP certification, DIACAP provides a standard for identifying, implementing and validating standardized information assurance controls.
FEDRAMP
FedRAMP is a government-wide program that provides a standardized approach to security assessment, authorization, and continuous monitoring for cloud products and services.
SOC 3
The SOC 3 is a general use public report of a service organization's controls over its systems relevant to security, availability, processing integrity, confidentiality, or privacy. The SOC3 report differs from the SOC 2 report, in that it is meant for public
consumption.
SSAE-18
Also known as Statement on Standards for Attestation Engagements (SSAE) No. 18, Attestation Standards: Clarification and Recodification. An internationally recognized accounting standard issued by the Auditing Standards Board of the American Institute of Certified Public Accountants (AICPA).




Energy Star
Energy Star is a government-backed labeling program that helps people and organizations save money and reduce greenhouse gas emissions by identifying factories, office equipment, home appliances and electronics that have superior energy efficiency.
NIST
NIST SP 800-53 Rev. 4 under Marking. The means used to associate a set of security attributes with objects in a human-readable form in order to enable organizational, process-based enforcement of information security policies.
Uptime Institute MO Site Award
Uptime Institute Issued Awards. Uptime Institute has issued 1944 awards in 109 countries for our Tier Standard, M&O Stamp of Approval and Efficient IT programs. These awards represent the 3rd party validation of data center designs, constructed facilities, operational plans and overall efficiency.
ISO
ISO compliance refers to ISO 9001, a quality management standard used by Organizations to prove that they provide services and/or products that meet certain requirements. These requirements are regulated by the ISO 9000 series which is the only quality standard that businesses can aspire to.




SOC 1
SOC 1 compliance affirms the security of your services and gives your organization the ability to provide clients with evidence from an auditor who has actually seen your internal controls in place and operating.
Uptime Institute Tier III Constructed
A Tier III data center is concurrently
maintainable, allowing for any planned maintenance activity of power and cooling systems to take place without disrupting the operation of computer hardware located in the data center. In terms of redundancy, Tier III offers N+1 availability.
PCI
The Payment Card Industry Data Security Standard (PCI DSS) is an information security standard for organizations that handle branded credit cards from the major card schemes.
The PCI Standard is mandated by the card brands but administered by the Payment Card Industry Security Standards Council. The standard was created to increase controls around cardholder data to reduce credit card fraud.
FISMA
FISMA compliance is data security guidance set by FISMA and the National Institute of Standards and Technology (NIST). NIST is responsible for maintaining and updating the compliance documents as directed by FISMA.


SOC 2
SOC 2 is an auditing procedure that ensures your service providers securely manage your data to protect the interests of your organization and the privacy of its clients. For security-conscious businesses, SOC 2 compliance is a minimal requirement when considering a SaaS provider.
Uptime Institute Tier III Design
A Tier 3 data center is a location with
redundant and dual-powered servers,
storage, network links and other IT
components. It is one of the most
commonly used data center tiers,
where IT components are powered
with multiple, active and
independent sources of power
and cooling resources.
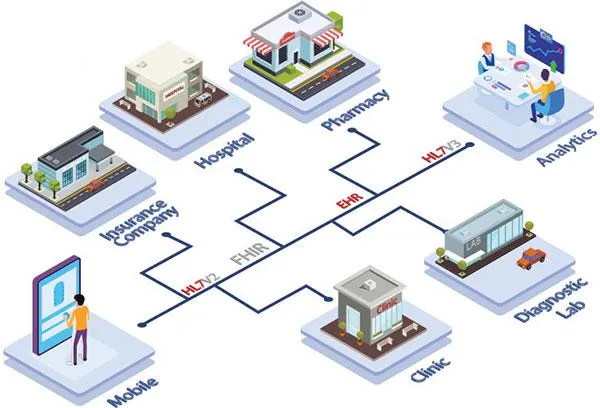
HL7
For a large healthcare organization, the amount
of clinical and administrative data constantly rolling in can be
staggering. A robust data analytics infrastructure is essential for
delivering actionable insights to providers and staff, but the process
of balancing scale and usability can be difficult to manage.
As healthcare technology company, we manage a
platform that aggregates and normalizes clinical data. This lets
organizations use information from any certified EHR in other
applications.
The platform ingests HL7 data from different
providers and in different formats. Then it maps into other formats for
use downstream.
Integrate. Analyze. Understand
The foundation of 'data analytics' is the data
itself. As they say, 'garbage in, garbage out'. If you're struggling to
reconcile and analyze information from many sources, we can help.
You can pull HL7 data sources into business intelligence tools or Excel.
ICD10
More Abundant, Granular Healthcare Data Fosters Deeper Analytics
ICD-10 dramatically increases the volume,
variety, and specificity of healthcare data. Whereas before much of the
detail about a patient's condition, regimen of care, and outcome of that
care was masked by general or unspecified codes, these elements and
insights are now standardized and clarified on claims.
ICD-10's specificity has made claims an even
richer source of data. This change brings with it certain
challenges—specifically, managing and extracting actionable information
from increasingly massive data sets.
Why are some patients readmitted—but not others?
That's a trick question, because how can a researcher ever know why
patients readmit if they aren't even sure (at the data level) what
conditions people are really suffering from?
Now with the additional
granularity of ICD-10 and the data-mining capabilities to uncover and
correlate other data points such as care history, demographic
information, and comorbid conditions, researchers and analysts can
better see what's really driving readmissions because they can better
"see" the patient in the data.
Our Vision
Our vision is to be at the forefront of healthcare innovation, where artificial intelligence and ethical practices merge to create sustainable, impactful changes. We aim to revolutionize patient care by integrating AI technologies that respect privacy and enhance diagnostic and operational efficiencies. By focusing on ethical AI use, we strive to mitigate risks and maximize benefits, providing a model for the future of intelligent healthcare solutions.
Technology Stack
We know data is important and we take all the care to ensure data is
secure. We structure the data in an efficient way to handle the
request-response of APIs for storing and retrieving data.
Different technologies we work on are: NET, C#, VB.Net, MS SQL Server, Xamarin, React, React Native
Proprietary

Open Source

Our Office
154 Bella Katy Rd. Suite 200, Katy, TX 77494
Primary Datacenter
1510 Primewest Parkway, Katy, TX 77449
